Activate Intelligence Requirements
Align deliverables with requirements from security operations, cyber risk management, and the business. Create, identify, and disseminate relevant, high-value threat intel to customers to help them proactively respond to threats.
Go from Undocumented to Actionable Intel Requirements
Intelligence requirements are simple to create, manage, and optimize directly within the platform, decreasing reliance on external tools like wikis, docs, and spreadsheets.

Easily Capture and Action Intelligence Requirements
Creating and actioning intelligence requirements is easy. A requirement creation wizard and AI-recommended keywords ensure precise and efficient intel tracking tailored to customer requirements.
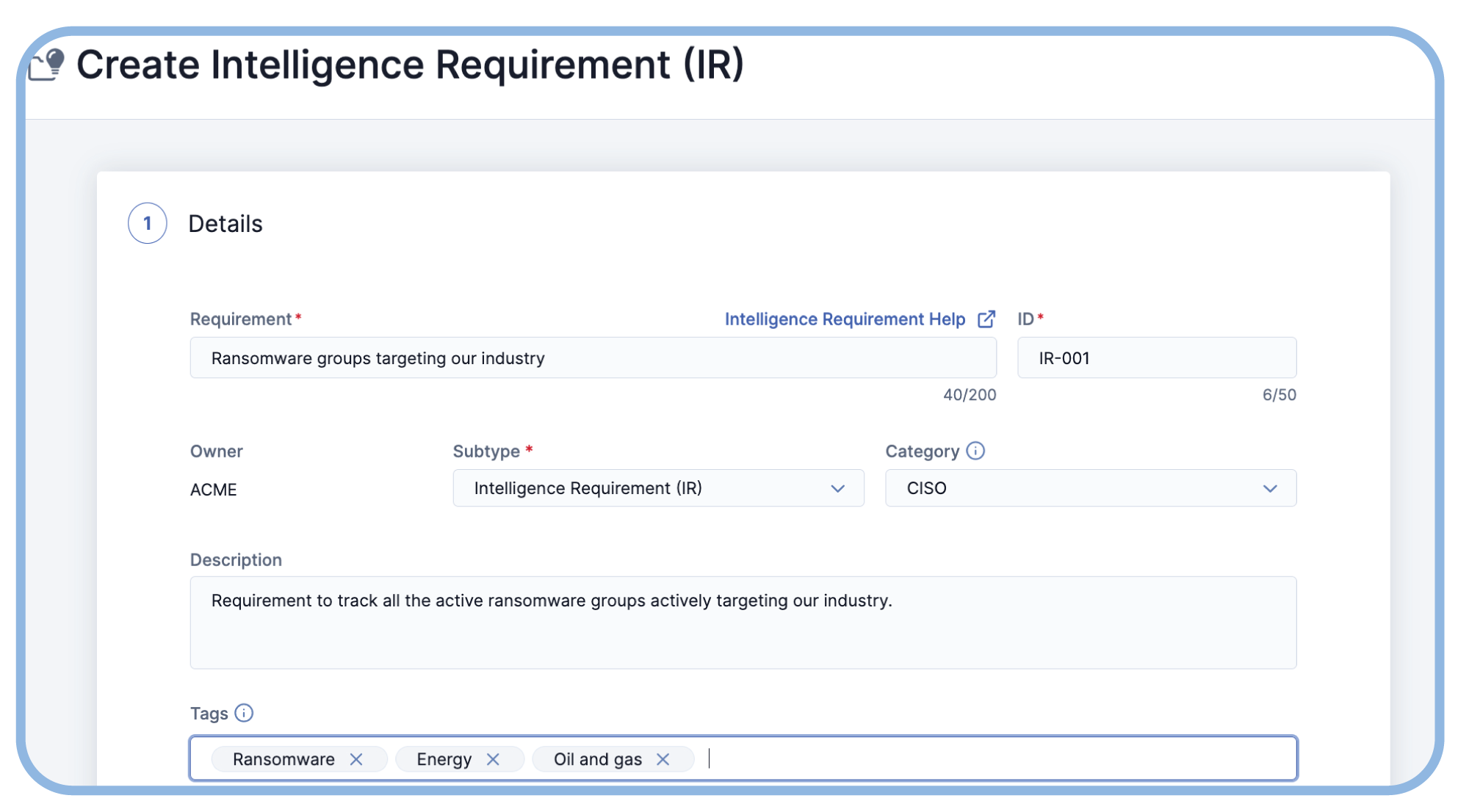
Centralize Intelligence Requirement Management
Intelligence Requirements allows analysts to capture and enable a wide variety of intel requirements in a central location to maximize CTI program planning, direction, and value creation.

Intelligence Requirements are Critical for Threat Intel Success
Operationalize Your Intel Requirements
Learn what’s needed to capture and implement intelligence requirements for a successful TI Ops program.
Creating Intel Requirements Isn’t Hard
Dive into the five-step process for creating intelligence requirements.
Streamline Your Threat Intel Function
ThreatConnect experts discuss the role of intelligence requirements in an effective and efficient TI Ops program.