Prioritize Vulnerability and Exposure Response
To stop attacks, you need to know which of the myriad of vulnerabilities to address first, and time is of the essence. Unify threat and vulnerability intel to enable rapid prioritization and justification for remediating attack surface exposures.
Aggregate and Centralize Vulnerability Intelligence
Automate the collection and analysis of vulnerability intelligence from commercial and industry sources, enrich it with threat intel and vulnerability scan data, and provide an enterprise-wide picture of critical vulnerabilities and potential impacts.
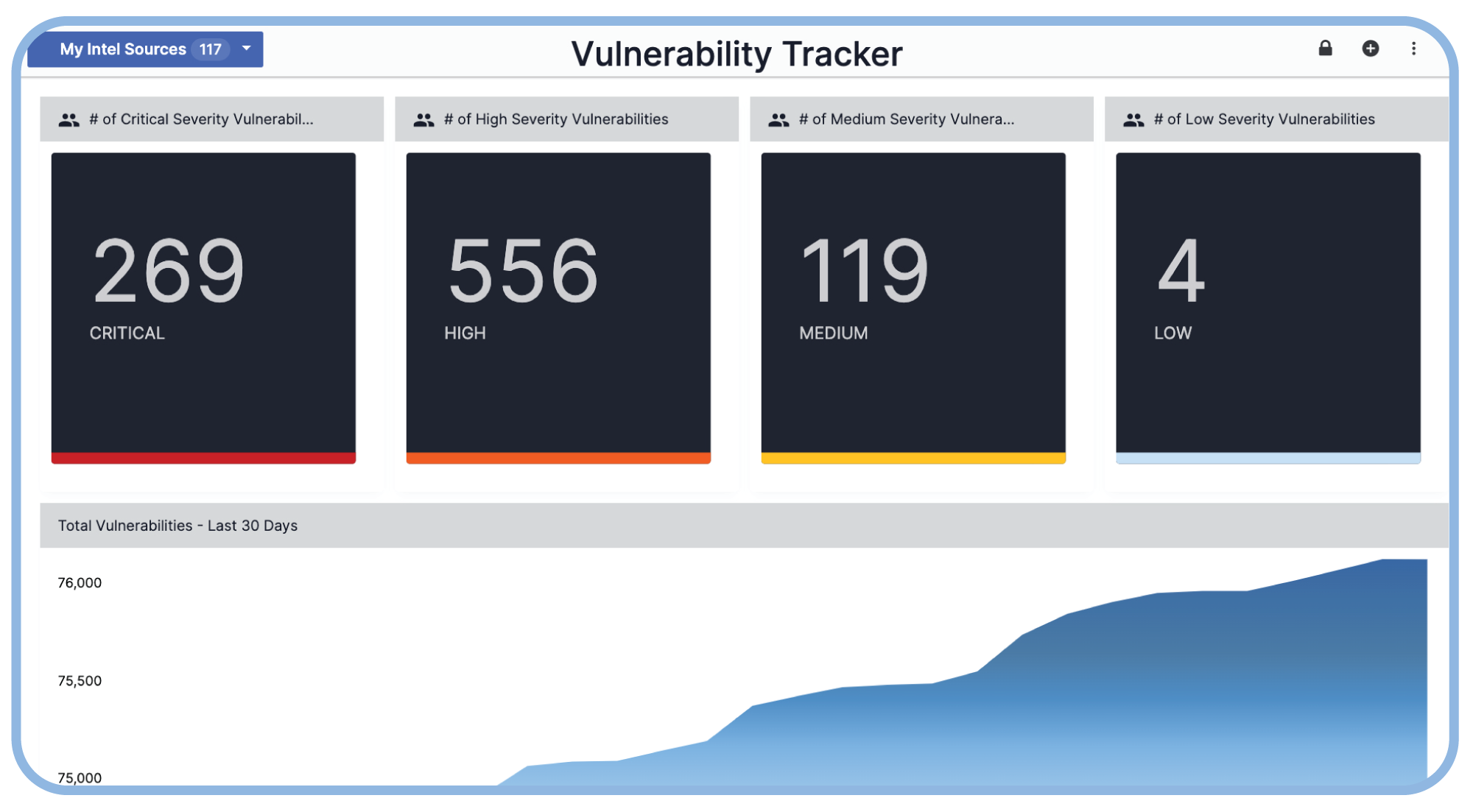
Visualize Vulnerability Impact Using Threat Graph
Use Threat Graph to quickly understand the relationships and associations with your threat and vulnerability intel to ensure the threat landscape is assessed and used to prioritize vulnerability response activities.
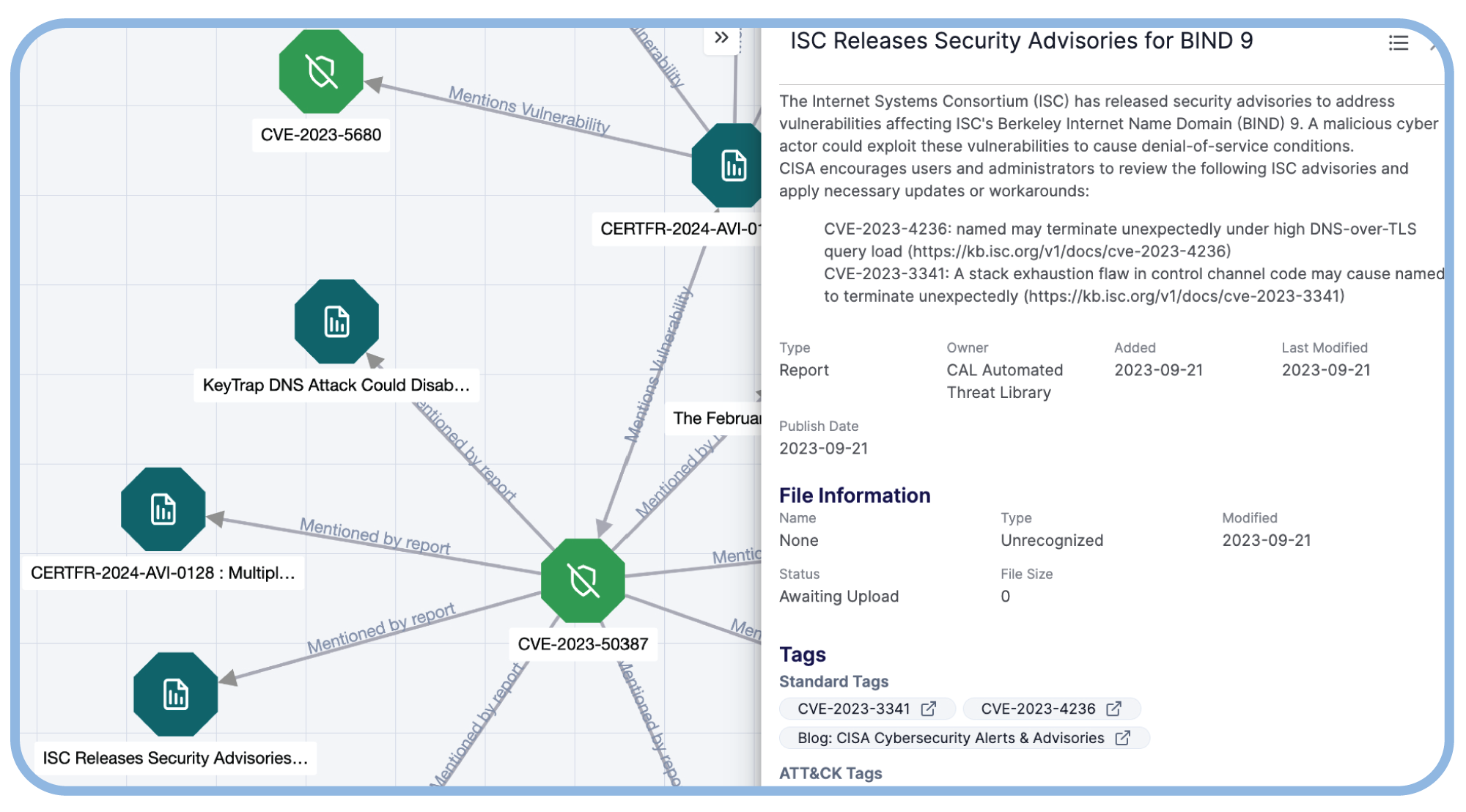
Share Intel Quickly and Efficiently
Ensure the vulnerability management team and leadership are informed on high-risk exposures to the business. Quickly create and disseminate intelligence reports with native reporting.
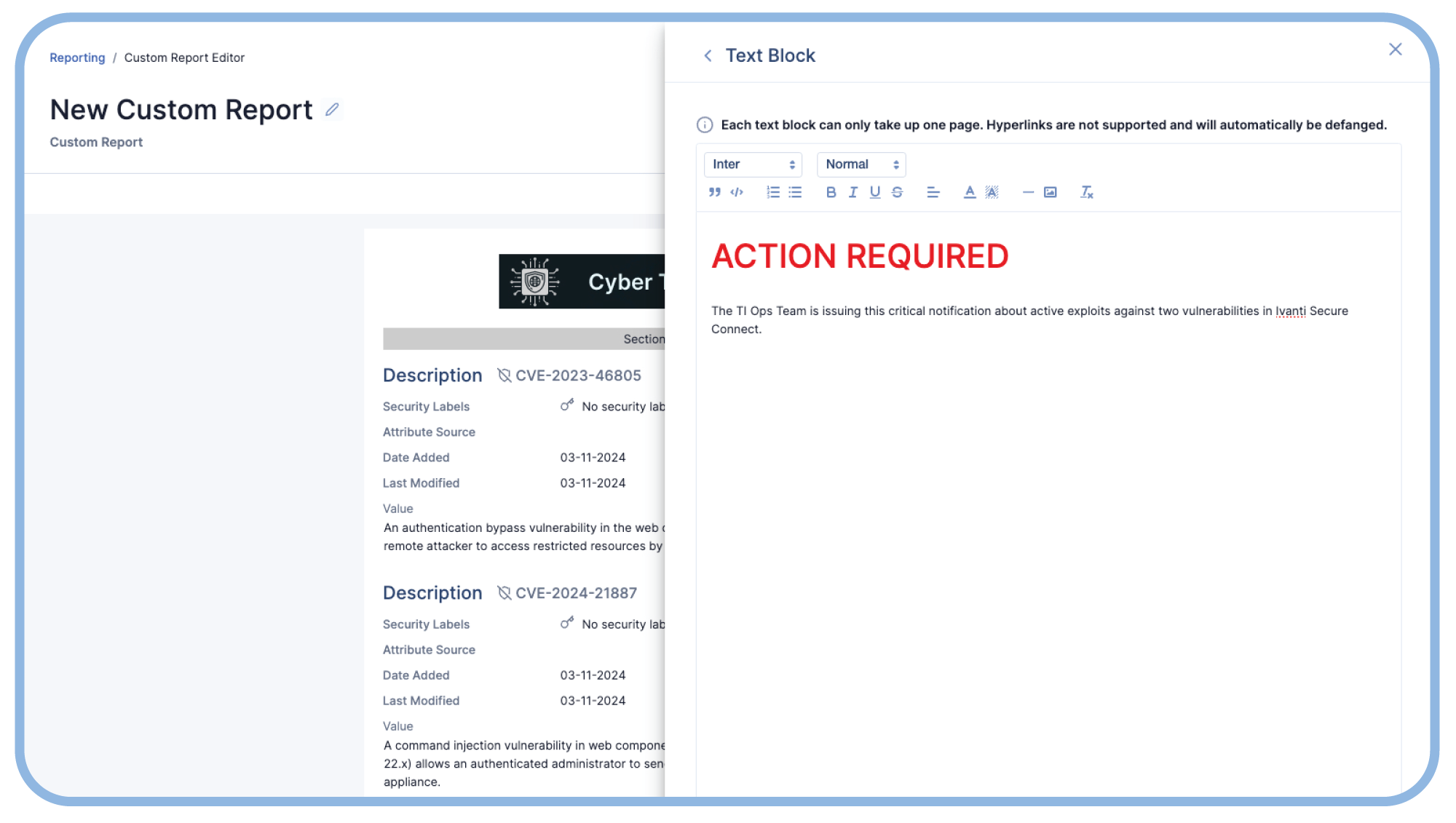
Focus on the Vulnerabilities that Matter
Intel-driven CVE Enrichment and Remediation
Learn how to use threat intelligence to improve vulnerability analysis and drive remediation efforts.
Easily Integrate Vulnerability Management
Out-of-the-box apps and playbooks make it easy to integrate popular vulnerability management solutions.
See the ThreatConnect TI Operations Platform in action
Experience ThreatConnect and see how you put vulnerability intelligence into action.